How to Recover IT Environment from Ransomware Attack?
2023-04-13 | Nick Zhao
Are you looking for a ransomware protection solution? Try Vinchin Backup & Recovery to backup IT environment with storage protection.
What is ransomware?
Ransomware is a kind of malware that can encrypt user’s files to ask for ransom from the victims. The encrypted files often include important production data such as database data and virtual machine data, so that the victim can do nothing but pay the ransom, usually bitcoin.
Unfortunately, even though you have paid the ransom to attacker, the encrypted file might not be decrypted for some reason. Therefore, it will be a dilemma that you might lose the important data and suspend your business without paying the ransom or take a chance to pay the ransom but still lose the data and leave the business suspended at last.
Ransomware varies very fast and is often immune to ordinary anti-ransomware software.
How does ransomware arrive in your IT environment?
There are mainly two ways. IT departments often warn the staff that do not click links or open attachments from strangers’ emails because this might download malware to your computer and then infect the whole production environment.
What’s more, there are always holes in operating system and when the attackers find the holes, they can use them to log in to your server to run the ransomware.
How does ransomware encrypt your files?
After ransomware is downloaded to a local machine, it will start to destroy your IT system automatically.
Firstly, it will delete the sample to escape detection.
Then, it will use the Internet to connect to the attacker’s server to upload the information of the local machine, download the public key, and encrypt files by writing the public key to the register and tampering and encrypting other files.
It is nearly impossible for others to decrypt the files except the developer.
After encryption is completed, it will modify the wallpaper to present the notification from the attacker and urge the users to pay the ransom.
How to prevent ransomware attack?
Ransomware is horrible but you can defend your IT system against it with some useful methods.
Update OS and Apps
Since ransomware can invade your system with holes you should subscribe to the vendor to get the latest news and update the operating system and applications in time.
Use security software
Firewall should be at least enabled as the basic ransomware protection solution. Paid enterprise anti-ransomware software will be a good solution and don’t forget to scan IT environment regularly.
Create data backup
Files getting locked by ransomware might be the last thing you want to see but you can still have the chance to recover your data.
Data backup is crucial for ransomware protection because it will reduce the difficulty and cost of data recovery. It would be better to copy data backup to a secondary datacenter or send it to the cloud in case that data backup itself is infected.
This should be taken seriously by small businesses because according to statistics, most ransomware attacks target small businesses because they often don’t have data backup.
Perform trainings
The common staff might not be sensitive to cyberattack so that IT department should perform trainings for the employees.
The content can include things like what is cyberattack and the consequences of it. Also, they should be told something to help prevent ransomware like don’t click the links or open a suspicious attachment in the email from an unknown sender.
Network segment
To prevent ransomware from spreading in the whole IT environment, you can divide the whole network into smaller, distinct sub-networks. With the independent firewall, security control, and access control, you can isolate and delete the ransomware to prevent further spread.
Endpoint security
Properly configuring the router can help defend against malicious scanning, stop access to the inactive endpoints, and convert the common port number to a unique port number. In addition, endpoint protection platform and endpoint detection & response can also help resist cyberattack.
Zero trust
Zero trust regards all the applications for connecting the devices as potential threats and will distrust them until their identity are verified.
With zero trust, anyone wishes to access the device will be required to verify identity, like multi-factor authentication and network access control.
Whitelist
Application whitelist can decide which programs can be executed to prevent running a virus or trojan.
How to recover IT environment from ransomware attack?
If your IT environment is unfortunately locked by ransomware, you can do something to try recovering data. You should isolate the infected machines in case of further spread.
Contact your software vendor
Some vendors have the internal solutions for ransomware data recovery and it will be fast and economical.
Restore from data backup
When you have data backup, you can wipe the infected machine first and then easily recover data from data backup.
Turn to ransomware recovery expert
If you really want the data back without paying the ransom, you can procure ransomware recovery service from an expert but it might be costly.
Backup your IT environment with storage protection
Vinchin Backup & Recovery is a professional backup and disaster recovery solution to help you backup IT equipment such as physical/virtual server, database, etc. There will be a user-friendly web console to help you easily create backup and restore jobs.
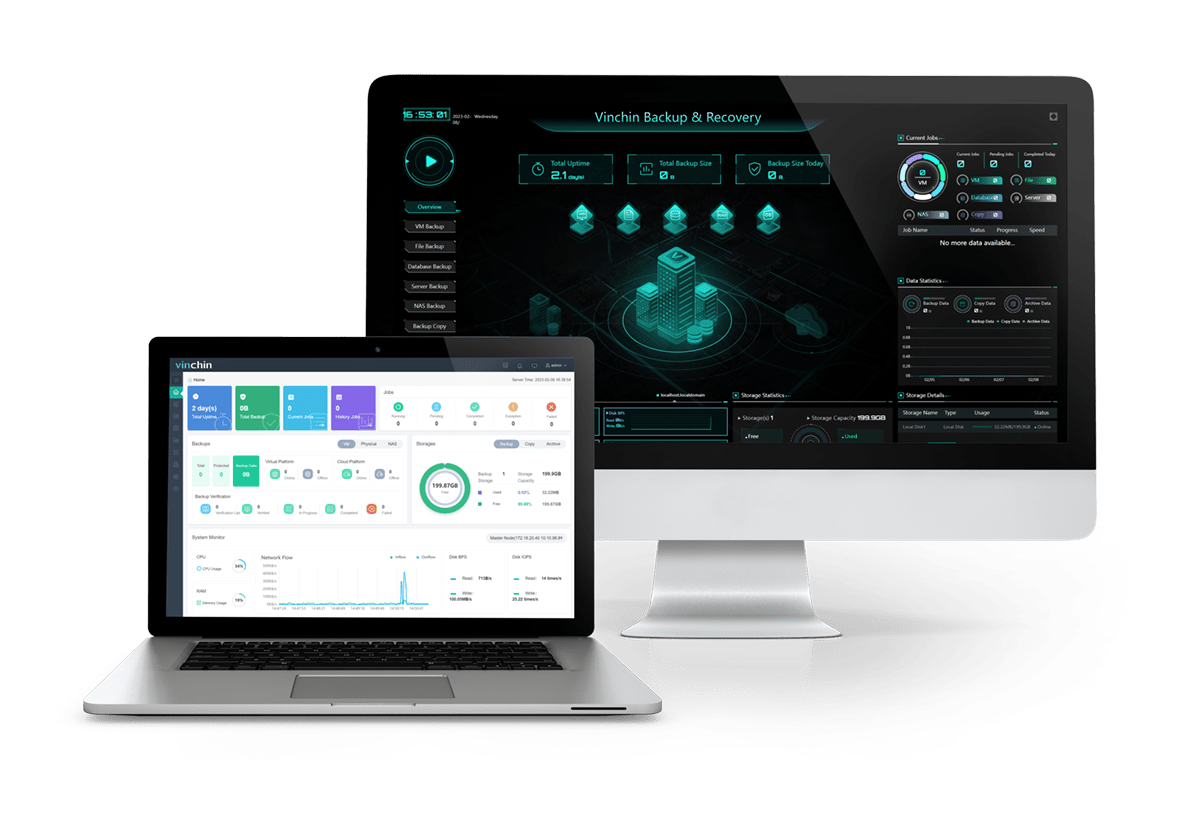
Vinchin storage protection can help effectively defend ransomware because data in the backup storage won’t be tempered by ransomware. The I/O will be monitored in real time to prevent files in backup storage be modified or deleted by non-Vinchin application.
If your IT environment is infected by ransomware, you can deploy a new environment and quickly import the backup data and then restore VM and servers to recover business.
Vinchin Backup & Recovery has been selected by thousands of companies and you can also start to use this powerful system with a 60-day full-featured free trial. Just click the button to get the installation package.
Sum Up
Ransomware is rampant on the Internet and has caused billions of losses to companies but companies can also prevent being attacked by ransomware by knowing how it works and making preparation. Even though IT environment is infected at last, there are still ways to recover the encrypted data.
Vinchin Backup & Recovery can help backup your IT environment with storage protection so you can easily resist ransomware attack. Don’t miss the free trial.
Share on:
 English
English