Linux-Based Ransomware Cheer Attacks VMware ESXi Devices
2022-06-02 | Vinchin Official

A new ransomware strait“Cheers”aimed at VMware ESXi servers is detected. Cheers is a Linux-based ransomware whose malicious actors launch to target VMware ESXi servers, a bare-metal hypervisor running virtual machines widely used by large enterprises and organizations.
Ransomware attacks against VMware ESXi systems have been rising recently, among which the most notorious are LockBit and Hive. Being the most popular virtualization platform, VMware has been deployed by over 500,000 customers throughout the world, these cyber attacks against it infecting numerous virtualized systems, related devices and extorting generous payment.
How it works?
After Cheers terminates the VMware ESXi server with following command line, it encrypts files with .log, .vmdk, .vmem, .vswp, and .vmsn extensions and renames the successfully encrypted flies as .Cheers extension. Those extensions are related to ESXi snapshots, log files, swap files, paging files and virtual disks.
“esxcli vm process kill –type=force –world-id=$(esxcli vm process list|grep ‘World ID’|awk ‘{print $3}’)”
It's a wonder that Cheers renames files before encryption, therefore, if the access permission for renaming is not granted, the encryption cannot proceed. The encryption uses a pair of ECDH public and private keys held by the criminals through Linux’s /dev/urandom to get a secret (SOSEMANUK) key and embeds it to the encrypted files. The public key used to generate the secret key will not be saved, one cannot combine it with the private key to produce a secret key. Thus, decryption relies on the cybercrime gang behind this.
After Cheers successfully encrypts the files, it will drop the note named “How to Restore Your Files.txt” that includes messages on what’s going on the files and links to sites of Tor data leak and payment negotiation. Finally, it displays certain console showing the encrypted data information for victims’ notice.
The new ransomware family appears in March 2022 according to the research of BleepingComputer, a technology website.
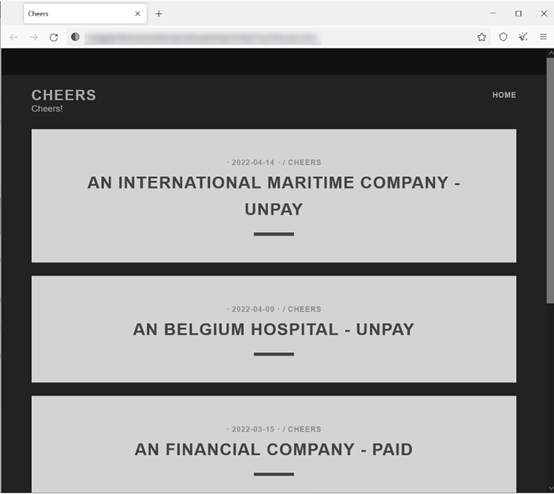
The data leak site Onion where Cheers extorts and presents victims lists 4 victims now. They are corporations of semi-large size and given 3 days to access the provided site in exchange for the secret key, or threatened to leak or resell the stolen files to other scoundrels.
What can be done for VMware ESXi users?
How to prevent ransomware?Since network intrusion happens anyway, virtualization servers are just the end targets for attacking. The effective backup of crucial data and orderly disaster recovery routine bulk large for virtualization users. Vinchin Backup & Recovery is a third-party data protection solution delivering efficient backup and complete data recovery for virtualizations including VMware.
Efficient VMware Backup: You can custom-made your backup strategies with specialized HotAdd transit, CBT technology and optional backup strategies for your business. The solution has backup storage protection securing VMware backups stored in Vinchin server that automatically denies any unauthorized access potentially to be ransomware.
Well-organized Disaster Recovery: You are allowed to build a DR center with offsite backup copies of the software by coping the backups to the remote site to minimize the economic damage from data loss. The copies are compressed, encrypted and transferred through proprietary network to maximize their safety as well as availability. Instant Recovery of the solution gets the target VMware VM up and run in 15s for almost seamless business continuity in the event of system failure or other disasters.
For more advanced VMware protection features, download 60 days free full-featured Vinchin Backup & Recovery and establish a DR plan in order.
Share on:
- Tag:
-
Company News
60-DAY FULL-FEATURED FREE TRIAL
- No credit card required
- Get started in 10 minutes