-
How to use EAC to configure circular logging exchange?
-
How to use PowerShell to configure exchange database circular logging?
-
How to backup Microsoft Exchange with Vinchin Backup & Recovery?
-
Conclusion
-
Circular logging FAQs
Circular Logging (Circular Logging) in Exchange Server refers to a special type of logging that is primarily used to control the growth of transaction log files. By default, Exchange Server generates a series of transaction log files to keep track of every modification made to the database so that these changes can be replayed when the database is restored, achieving data consistency and integrity.
Now, let's explore the process of how to configure circular logging of Exchange databases with two methods.
How to use EAC to configure circular logging exchange?
The Exchange Admin Center (EAC) is a web-based management interface provided by Microsoft Exchange Server to manage and configure various features and services of Exchange Server. Through the EAC, administrators can easily enable or disable ring logging.
To enable exchange database circular logging, following these steps:
1. In the EAC, go to Servers > databases
2. Select the mailbox database > click it
3. Check or uncheck the Enable circular logging checkbox > click Save
How to use PowerShell to configure exchange database circular logging?
PowerShell provides a scripted approach to managing Exchange Server, allowing administrators to write scripts to automate tasks. This is especially useful for large deployments as it saves a lot of time in manual operations and reduces the risk of human error. By using PowerShell, administrators can easily enable or disable ring logging.
This example enables circular logging for database DB1.
Set-MailboxDatabase DB1 -CircularLoggingEnabled $True
This example disables exchange database circular logging DB1.
Set-MailboxDatabase DB1 -CircularLoggingEnabled $False
How to backup Microsoft Exchange with Vinchin Backup & Recovery?
Enabling and disabling circular logging is an important part of managing an Exchange Server environment. However, to ensure comprehensive data protection and quick recovery from potential data loss, it's crucial to implement a robust backup and recovery solution.
Vinchin Backup & Recovery provides an effective backup and recovery solution for Microsoft Exchange. Vinchin has a powerful enterprise-class backup solution tailored to protect Microsoft Exchange, whether deployed on virtual machines or physical servers. The solution ensures that Exchange data can be backed up highly reliably and securely anywhere - locally, offsite or in the cloud, including platforms such as Azure, Amazon S3, Wasabi and more.
Vinchin Backup & Recovery’s operation is very simple, just a few simple steps.
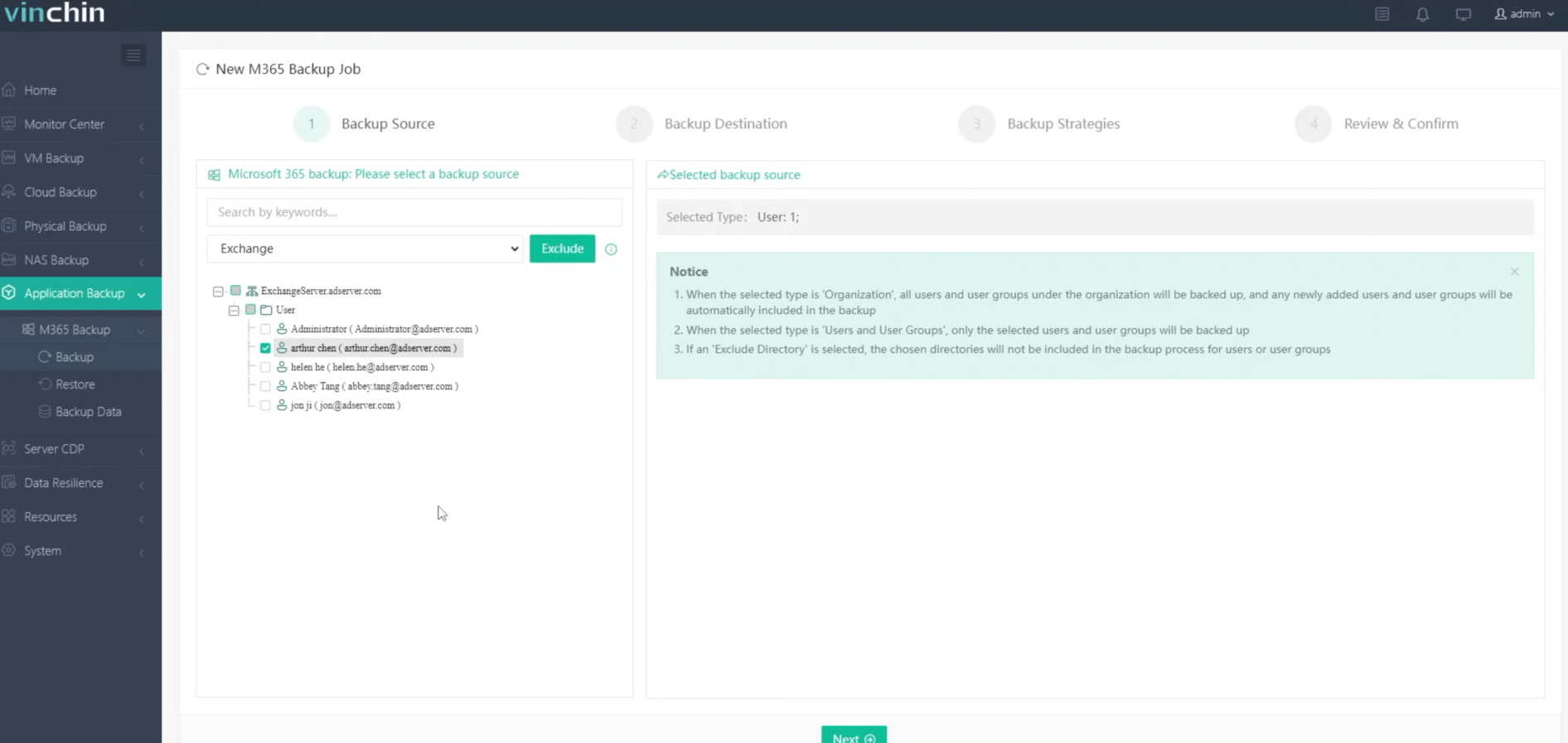
1. Just select Backup Source
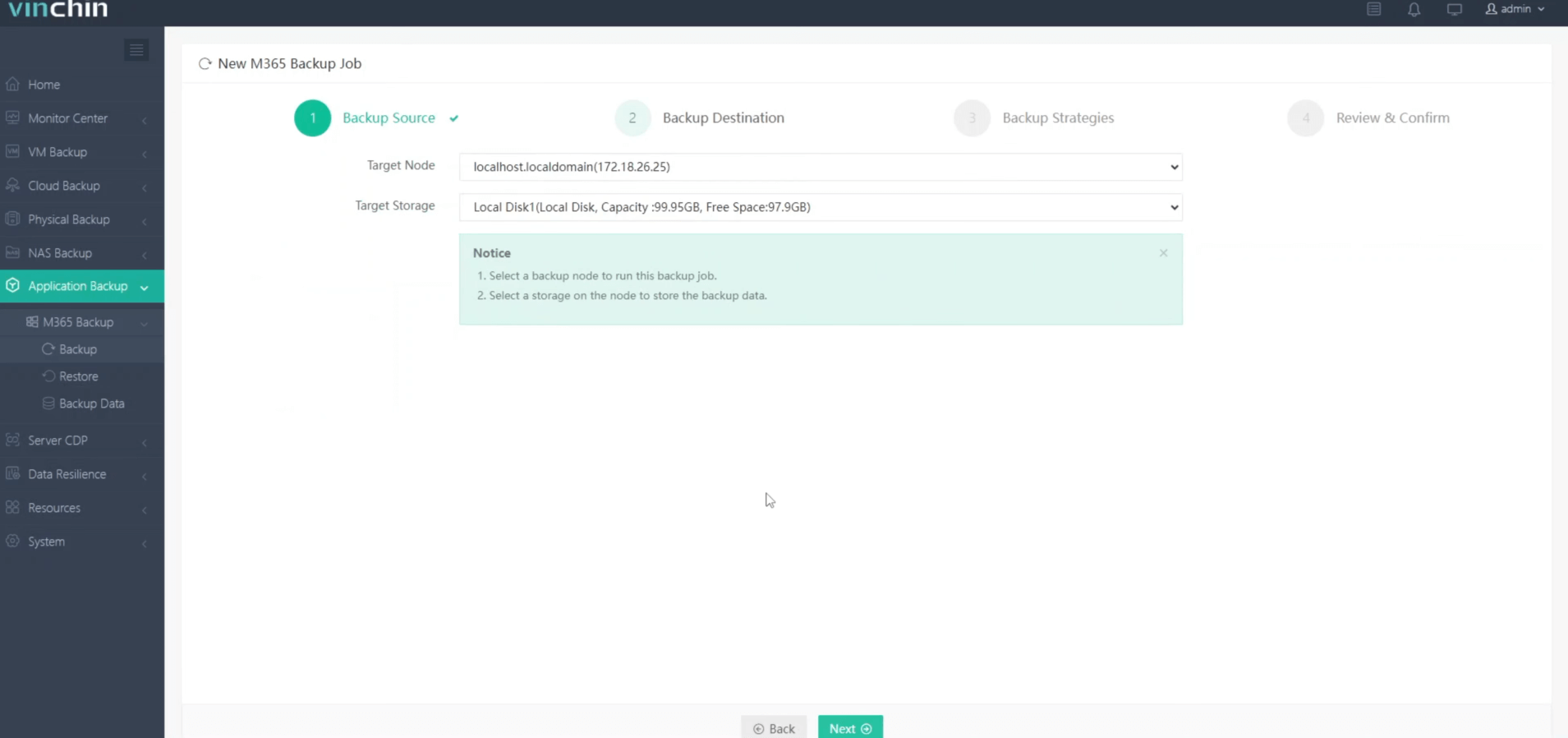
2. Then select backup destination
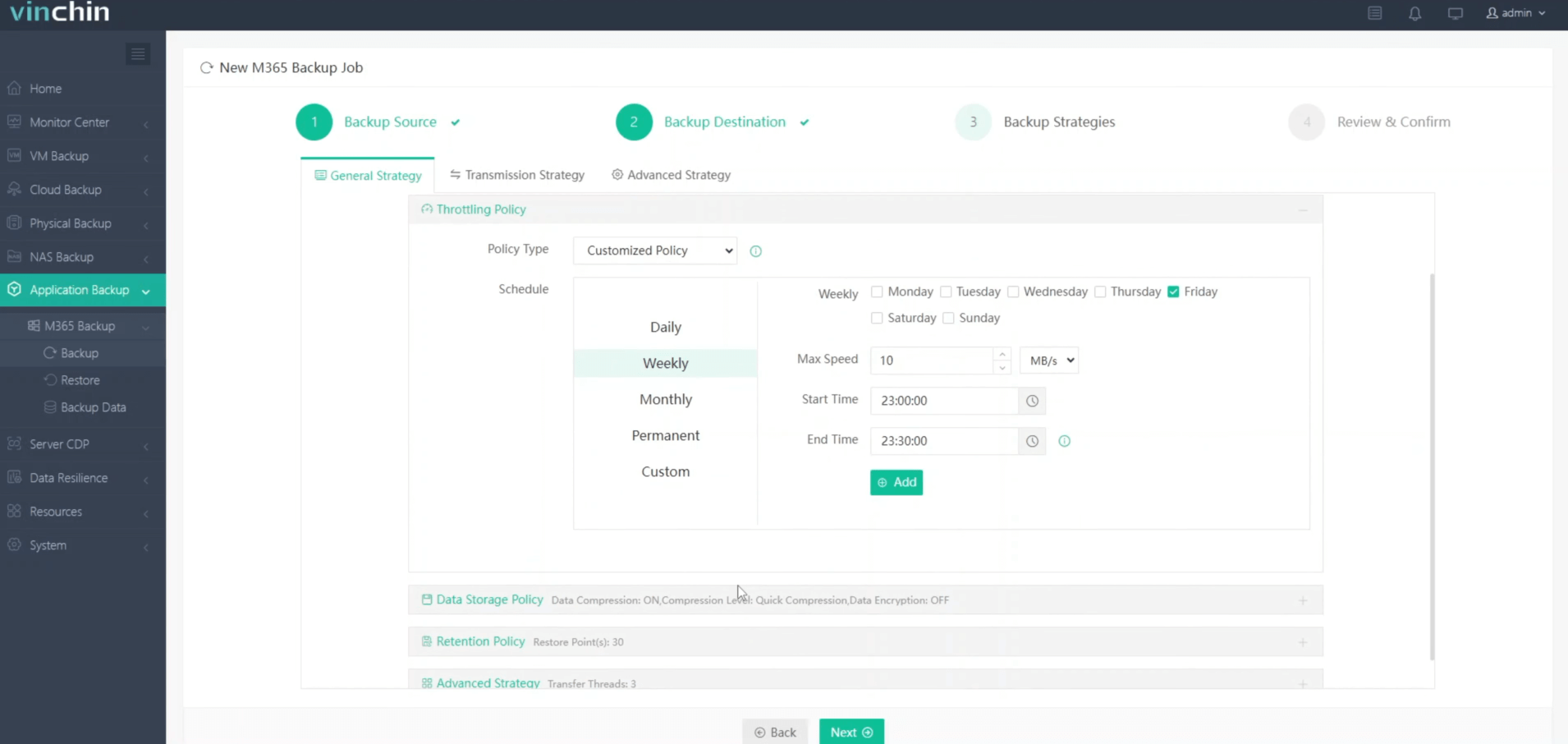
3. Select strategies
4. Finally submit the job
Vinchin offers a free 60-day trial for users to experience the functionality in a real-world environment. For more information, please contact Vinchin directly or contact our local partners.
Conclusion
Enable or disable Exchange circular logging using two methods: the Exchange Admin Center (EAC) and PowerShell. EAC offers a graphical interface, while PowerShell provides a scripted approach. For comprehensive Exchange data protection, use Vinchin Backup & Recovery.
Circular logging FAQs
Q1: What are the advantages and disadvantages of enabling circular logging?
Pros:
Saves disk space: reduces storage requirements, especially in environments with high log generation.
Reduces administrative work: reduces the need for administrators to periodically clean up log files.
Cons:
Restricted recoverability: because old log files are overwritten, it is not possible to use full log files for point-in-time recovery, only to the last full backup.
Cannot perform incremental backups: cyclic logging does not support incremental backups, all backups are full backups.
Q2: Is it possible to use circular logging in all environments?
A2: Cyclic logging exchange is suitable for small or test environments and is not recommended for use in production environments, especially if a strict data recovery policy is required.
Share on: