-
What is a DLP system?
-
Why is DLP necessary?
-
How DLP Works
-
Main Advantages of DLP
-
DLP-related System Requirements
-
How to backup VM and database with Vinchin Backup & Recovery?
-
Enterprise Data Loss Prevention FAQs
-
Conclusion
In today's digital age, data security has become the primary concern for both enterprises and individuals. With the rapid development of information technology, data breaches are occurring frequently, causing significant economic losses and reputational damage to companies. To address this, DLP (Data Loss Prevention) technology has emerged as an important means of protecting sensitive information.
What is a DLP system?
DLP, or Data Loss Prevention, is a set of technologies and strategies designed to prevent data breaches, misuse, or unauthorized access. It monitors and controls data flow to ensure that sensitive information is not leaked externally or misused by internal employees. DLP solutions typically include features such as data discovery, data classification, data protection, and data monitoring.
DLP can be divided into the following two types:
Integrated DLP: DLP is just a part of a product feature, usually used for quick compliance, analyzing content in a simple manner, and cannot share policies across different environments.
Enterprise DLP: Focused on parts related to DLP data content, typically comprising components for endpoints, networks, discovery, and cloud. Enterprise DLP offers complete and in-depth content inspection capabilities, supports centralized management, and policies can be applied across different scenarios. Currently, the Enterprise Data Loss Prevention market includes numerous products with a wide range of use cases, providing visibility into data usage and movement across the organization. It can dynamically enforce policies based on content and context when performing operations on data. EDLP addresses related threats to data through monitoring, alerts, warnings, blocking, and other responsive functionalities, including the risks of accidental data leaks and the leakage of sensitive data.
Why is DLP necessary?
With the rapid advancement of information technology, computers and the internet have become essential tools for daily office work, communication, and collaboration. However, while information systems improve work efficiency, they also impose higher requirements on the security of data storage and transmission.
The amount of data that needs protection is increasing. Personal information (accounts, phone numbers, addresses, etc.), intellectual property (product designs, R&D drawings, etc.), trade secrets (budgets, plans, payrolls, etc.)—any data leakage can cause immeasurable losses to an enterprise.
Legal regulations are becoming stricter. GDPR, HIPAA, and others require enterprises to protect data assets and prevent the leakage of sensitive information. Data leakage incidents expose enterprises to legal risks.
Data leakage is not always the result of hacking. Incidents of data leakage caused by internal employees, whether intentional or unintentional, are on the rise, such as mis-sent emails, lost USB drives, and printing of confidential documents.
Traditional security solutions fail to provide adequate data leak prevention. Traditional security solutions use conventional firewalls, intrusion detection systems, storage encryption systems, and other security devices to offer passive, cage-like protection by limiting data access or encrypting data across the network. This hinders data flow, fails to control leakages by authorized users, and cannot identify sensitive information for effective classification management and auditing of enterprise data.
How DLP Works
DLP technology can monitor, identify, and protect sensitive data in real time. The workflow is roughly as follows:
Data discovery: The DLP system first scans all data within the enterprise to identify sensitive information, such as personally identifiable information (PII), financial data, and intellectual property.
Data classification: Classifying the discovered sensitive data to formulate corresponding protection strategies.
Data protection: Ensuring the security of sensitive data during storage and transmission through encryption, access control, and other means.
Data monitoring: Continuously monitoring the flow of data to promptly detect and prevent any potential data leakage behavior.
The general model involves building a policy database that includes all detection strategies and definitions of sensitive data. When an employee performs a certain action (such as sending an email), the system scans to determine if this action complies with security policies and takes appropriate actions, such as blocking or warning. On top of this basic model, features like permission control, auditing, and endpoint control are added to create a comprehensive DLP solution. However, ensuring effective detection of unstructured data and protection against malicious behavior remains challenging.
Main Advantages of DLP
Protecting sensitive data: DLP effectively prevents data leakage both internally and externally, ensuring the security of customer and enterprise information.
Compliance: Many industries have strict data protection regulations, such as GDPR and HIPAA. DLP helps enterprises comply with these regulations, avoiding hefty fines due to violations.
Raising employee awareness: Implementing a DLP system can enhance employee awareness of data security, prompting them to handle sensitive information more cautiously.
Real-time response: DLP technology can monitor data flow in real time, immediately issuing alerts and taking corresponding actions when abnormal behavior is detected.
DLP-related System Requirements
1. ISO 27001
This explicitly requires enterprises to establish relevant measures to prevent data leakage and control sensitive operations on devices. ISO 27001 emphasizes conducting security audits, regularly checking and recording data access and usage to timely detect and prevent data leaks.
2. EU GDPR
The EU General Data Protection Regulation (GDPR) came into effect in May 2018 and is the first law in the EU specifically targeting personal data protection. This regulation stipulates the basic requirements, responsibilities, and obligations for personal data processing, including data security, transparency, and user control. Companies that violate this regulation face hefty fines and penalties.
3. US CCPA
The California Consumer Privacy Act (CCPA) in the USA came into effect in 2020 and is California's first law specifically aimed at consumer privacy protection. This act sets forth basic requirements, responsibilities, and obligations regarding the processing of consumers' personal data, as well as consumer privacy protection and data breach notification.
4. US HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) in the USA requires healthcare institutions and health insurance companies to protect patients' medical information and prohibits disclosing such information without patient consent. Violating this regulation can result in fines and other legal liabilities for companies.
The Personal Data Protection Act (PDPA) in Singapore was enacted in 2012. The main purpose of this law is to protect the privacy and security of personal data, especially in the context of the rapidly developing digital economy. PDPA requires enterprises to adhere to the "notification-consent" principle when collecting, using, and disclosing personal data and sets strict requirements for cross-border data transfer and data security protection. Additionally, PDPA includes new provisions for data breach notification and data portability rights to ensure that personal privacy aligns with international standards while enhancing Singapore's competitiveness in the global data protection compliance environment.
How to backup VM and database with Vinchin Backup & Recovery?
In addition to DLP systems, enterprises can enhance their IT security by using Vinchin Backup & Recovery to protect virtual machines and databases. Vinchin offers comprehensive backup solutions that support various hypervisors and database systems, like VMware vSphere, Hyper-V, Proxmox, XenServer, XCP-ng, Red Hat Virtualization, oVirt, Oracle Linux KVM, OpenStack, MySQL Database, Oracle Database, SQL Server, etc., ensuring business continuity with features like incremental backups and disaster recovery. It also helps organizations comply with data protection regulations such as GDPR by encrypting backups, automating scheduling, and providing long-term retention options. By combining DLP with Vinchin’s backup solutions, businesses can safeguard sensitive data, reduce risks, and maintain secure, recoverable IT environments.
It only takes 4 steps for you to backup VMs:
1.Select the backup object.
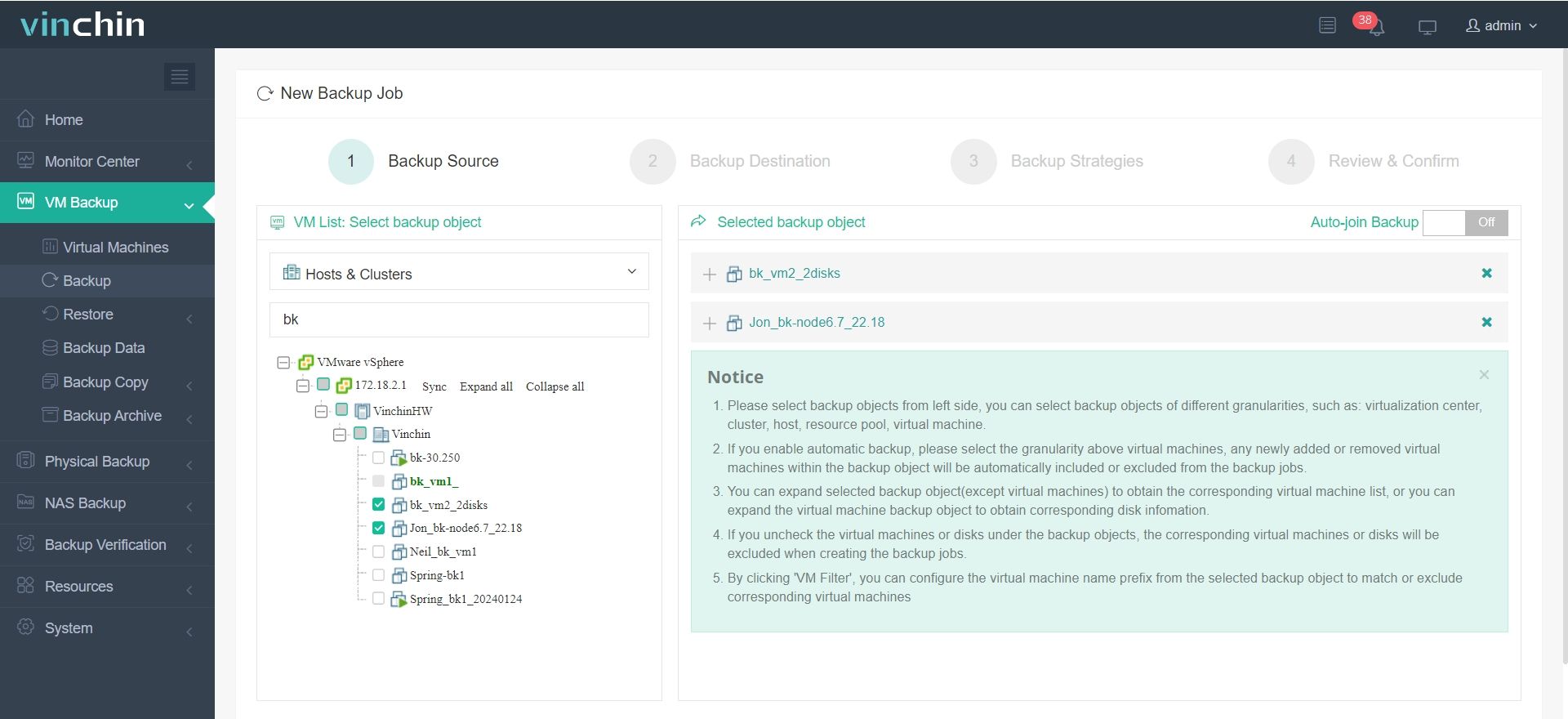
2.Select backup destination.
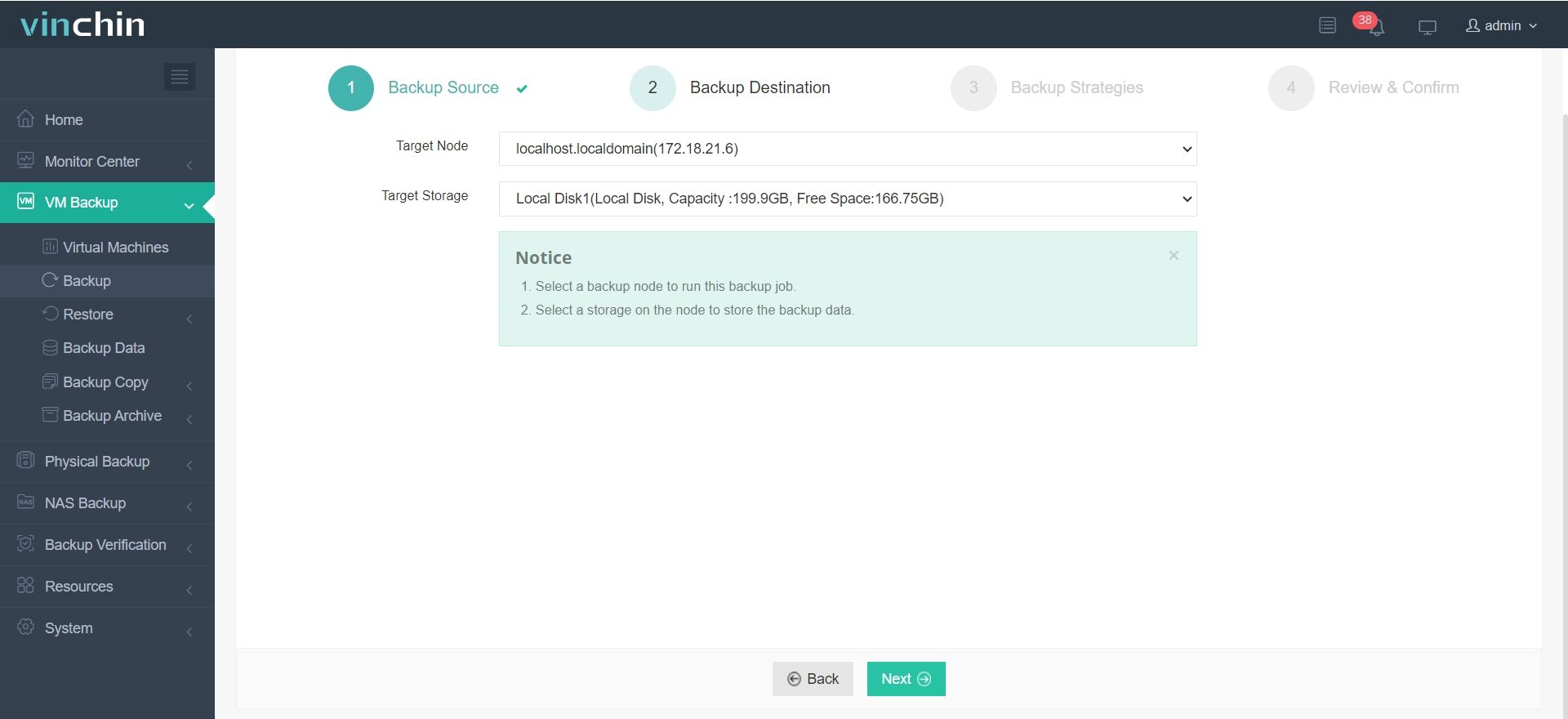
3.Configure backup strategies.
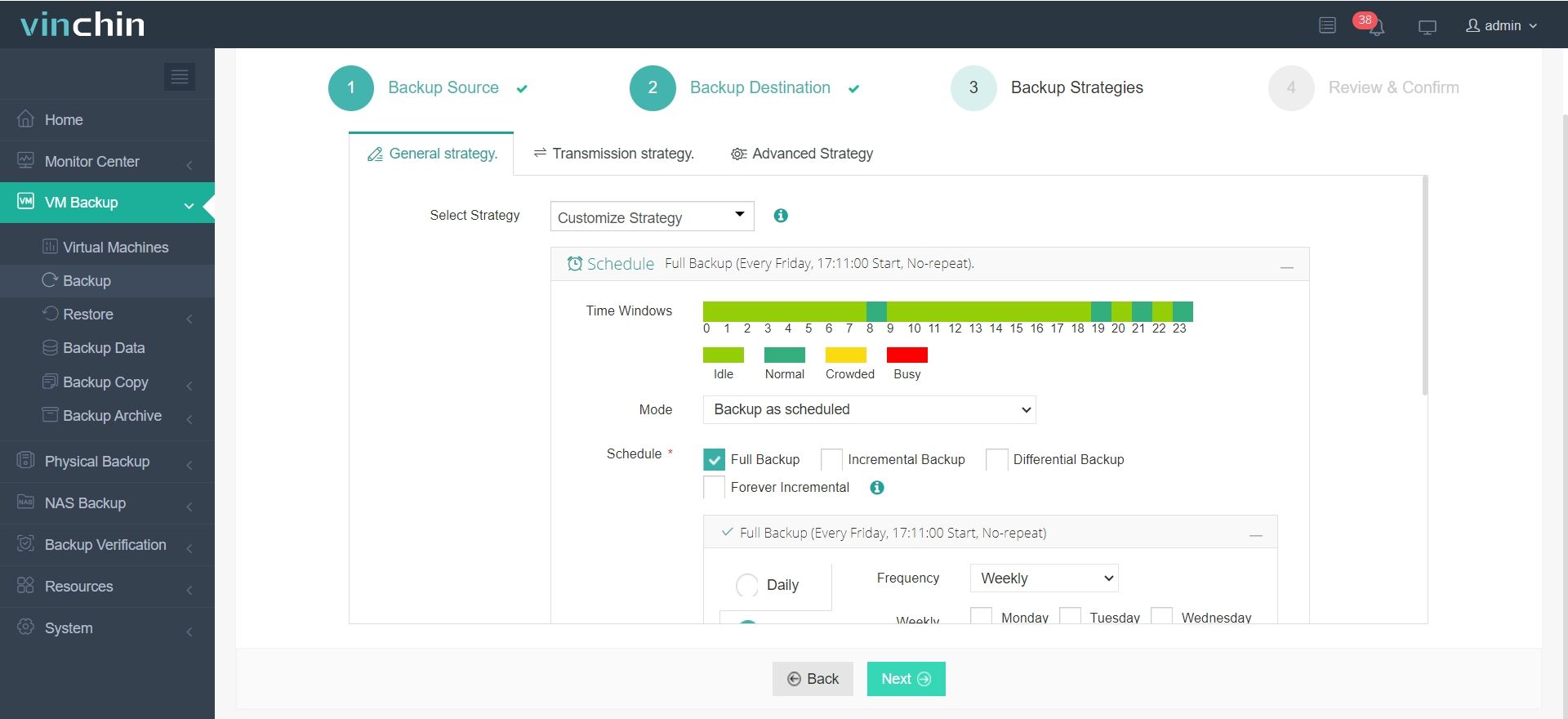
4.Review and submit the job.
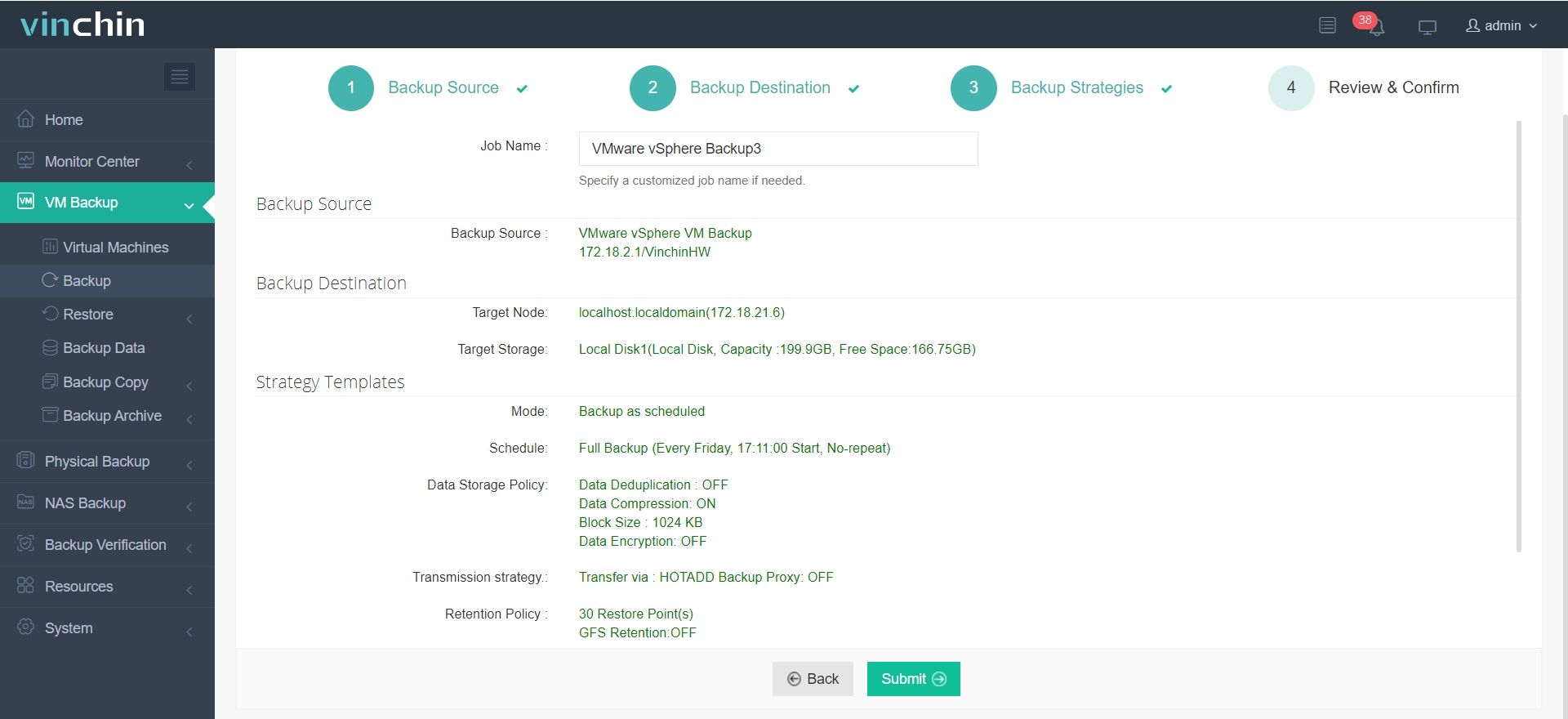
Vinchin Backup & Recovery has been selected by thousands of companies and you can also start to use this powerful system with a 60-day full-featured free trial. Just click the button to get the installation package.
Enterprise Data Loss Prevention FAQs
1. Q: How does DLP integrate with other security technologies?
Answer: DLP solutions can integrate with other security technologies such as firewalls, encryption tools, access management systems, SIEM (Security Information and Event Management), and anti-malware tools. This integration ensures a unified approach to security by providing comprehensive monitoring and enforcement of data protection policies across multiple layers of the IT environment.
2. Q: What is the difference between DLP and DRM (Digital Rights Management)?
Answer: DLP focuses on preventing data leakage and ensuring the security of sensitive data across all stages of its lifecycle. DRM, on the other hand, is focused on controlling how specific pieces of digital content are used and shared by authorized users. While DLP seeks to protect against data loss, DRM seeks to manage the rights and usage of specific content (e.g., preventing copying or redistribution of protected media).
Conclusion
DLP is crucial for protecting sensitive data, ensuring compliance with regulations, and improving overall information security in enterprises. By implementing DLP technologies and strategies, organizations can effectively mitigate the risks of data leakage and enhance their data protection posture.
Share on: