-
Why Should You Consider Hyper-V Security?
-
Hyper-V Security Best Practices
-
How to Protect Hyper-V with Vinchin?
-
Hyper-V Security FAQs
-
Conclusion
Hyper-V security is key for any data center today. Virtualization is widespread and protecting your virtual machines is a must. With threats on the rise, strong security practices can save time, money, and reputation. In this article, we explain why you should care about Hyper-V security, share best practices, and show you how Vinchin can help protect your environment. We also answer common questions on Hyper-V security.
Why Should You Consider Hyper-V Security?
Hyper-V is a leading type-1 hypervisor by Microsoft. It runs on many Windows systems and is common in enterprise settings. As more companies use virtual machines, the need for robust security grows. A breach can expose critical data and cause serious downtime. Recent patches and vulnerability alerts show that even Hyper-V is under attack. For example, Microsoft warned of a privilege escalation bug, CVE-2024-38080, that could let attackers gain SYSTEM privileges. This news underlines why you must take Hyper-V security seriously. Strong protection is not optional but a business need.
Virtualization offers many benefits but also adds risks. The host and guest operating systems can be weak points. A breach on the host can lead to compromised virtual machines. That is why every layer must be secured. With features like Secure Boot and Shielded Virtual Machines, Hyper-V provides built-in defenses. However, the security features only work if they are properly set up and managed. By following best practices, you reduce risks and guard against data breaches.
Hyper-V Security Best Practices
1. Secure the Hyper-V host
Use the smallest possible installation option such as Windows Server Core or Nano Server. Avoid the full GUI version. This reduces the attack surface. Keep the host operating system, firmware, and drivers up to date with the latest security patches. A patched system is less likely to be exploited by known vulnerabilities.
2. Protect your network
Use a separate network for management, live migration, and virtual machine storage. Enforce network isolation to keep traffic segmented. Virtual Network Isolation is a key defense that limits how far an attacker can move laterally if one part of your network is breached.
3. Secure your virtual machines by using Generation 2 VMs
Generation 2 Hyper-V VMs support Secure Boot and offer features such as a virtual Trusted Platform Module (vTPM). These settings help block unauthorized code from running during boot. Shielded Virtual Machines add another layer of security by encrypting virtual machine data and configurations. This means even if an attacker gains access to the physical server, the VM remains protected.
4. Integrate with BitLocker
This encryption tool protects virtual hard disks from unauthorized access. If disk files are stolen, encryption ensures that data remains safe without the correct keys.
5. Do not forget Host Guardian Services
This feature verifies that only trusted Hyper-V hosts can run shielded VMs. It acts like a gatekeeper. When a host is not approved, the service prevents the VM from starting. This measure is very effective in keeping your virtual environment secure.
6. Strong authentication
Use multi-factor authentication, certificate-based logins, or Windows Hello. Even if an attacker obtains credentials, they will struggle to bypass these additional security measures.
Following these best practices builds a robust security posture. Many companies have seen the benefits of layering security measures to reduce the risk of breaches. Staying vigilant and updating systems is the key to a secure Hyper-V environment.
How to Protect Hyper-V with Vinchin?
To bridge the gap between best practices and everyday operations, Vinchin offers a robust solution. Vinchin is a trusted software that supports many workloads. Its main focus is on virtual machine backup and migration, supporting mainstream platforms like Hyper-V, VMware, Proxmox, oVirt, OLVM, etc.
Vinchin can backup and restore your virtual machines quickly. It offters DR Lab to help automatically verificate the usability of VM backup. Vinchin also offers options for data retention and archiving. These features ensure that your backup data is safe from tampering and breach.
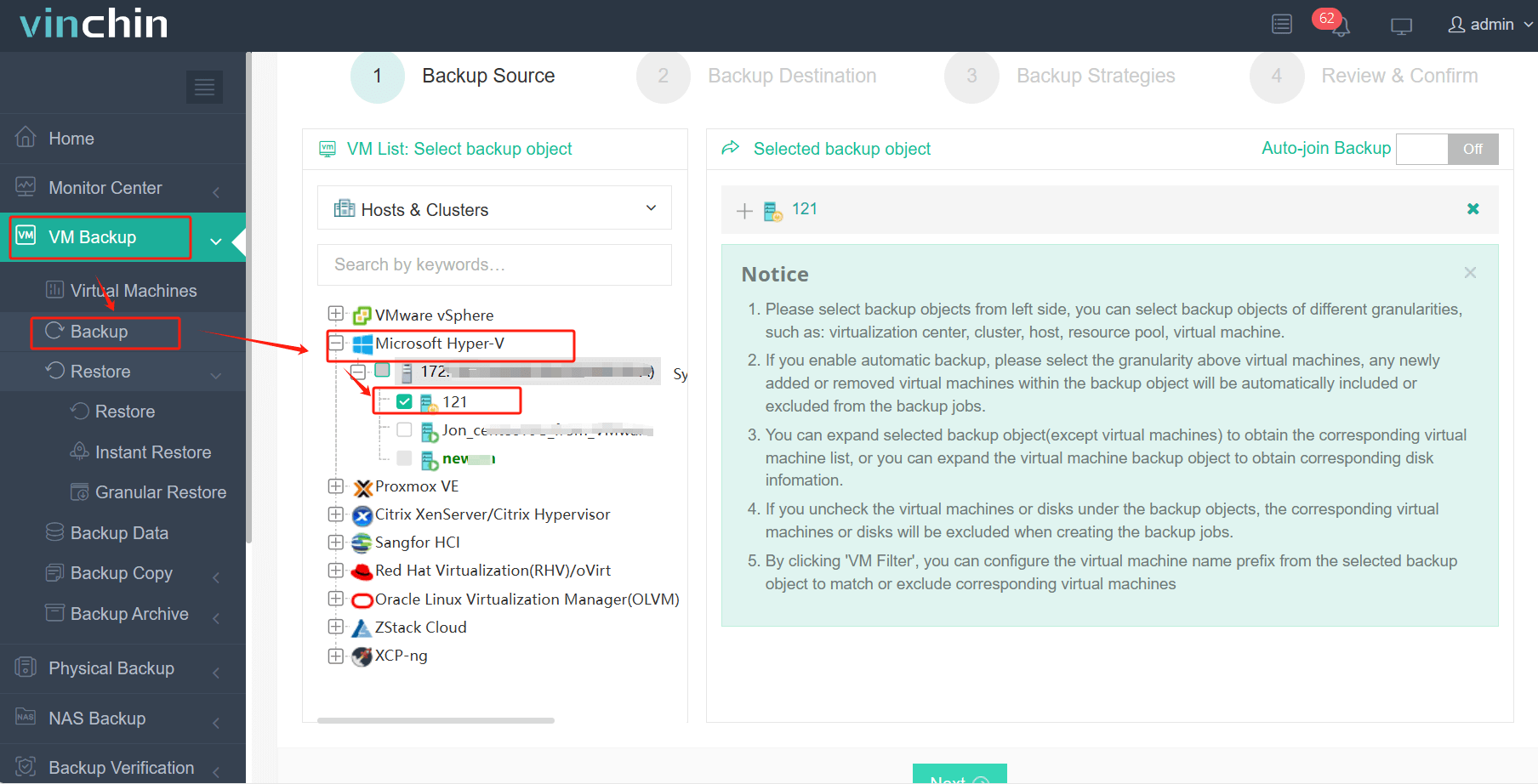
The Vinchin web console is simple to use so you can easily create a Hyper-V backup job:
1. Select the Hyper-V VMs
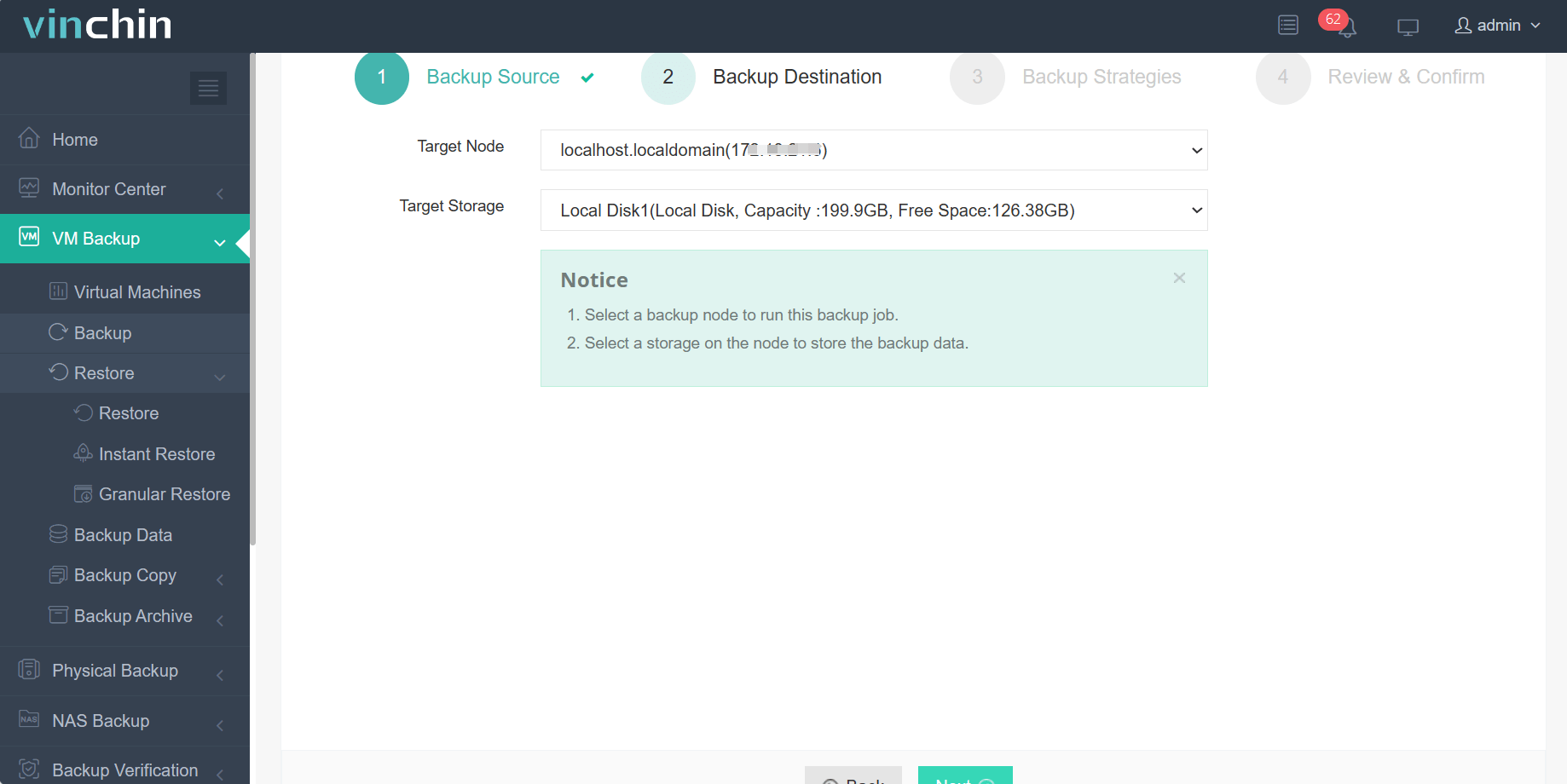
2. Select the backup storage
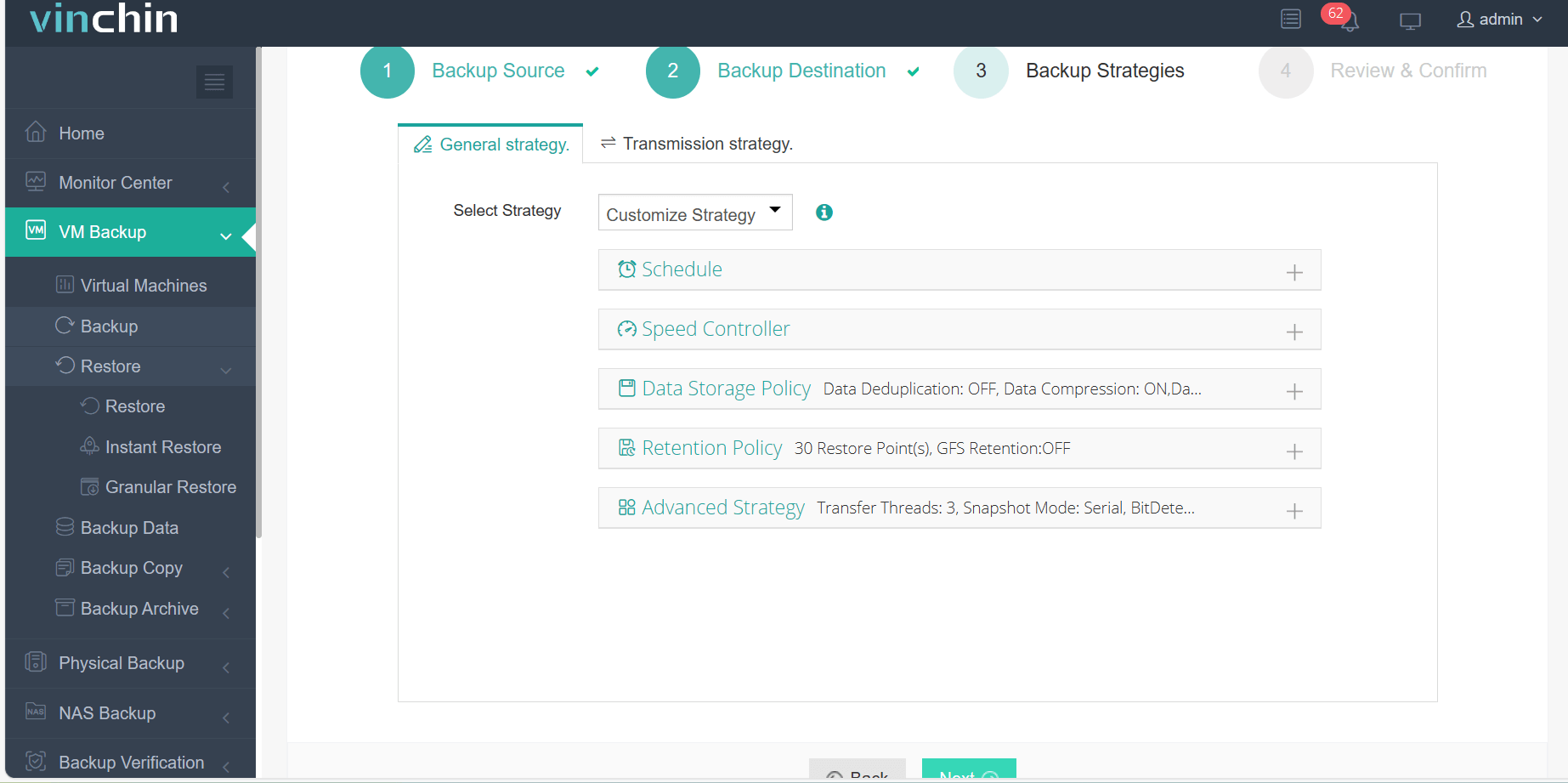
3. Select the strategies
4. Submit the job
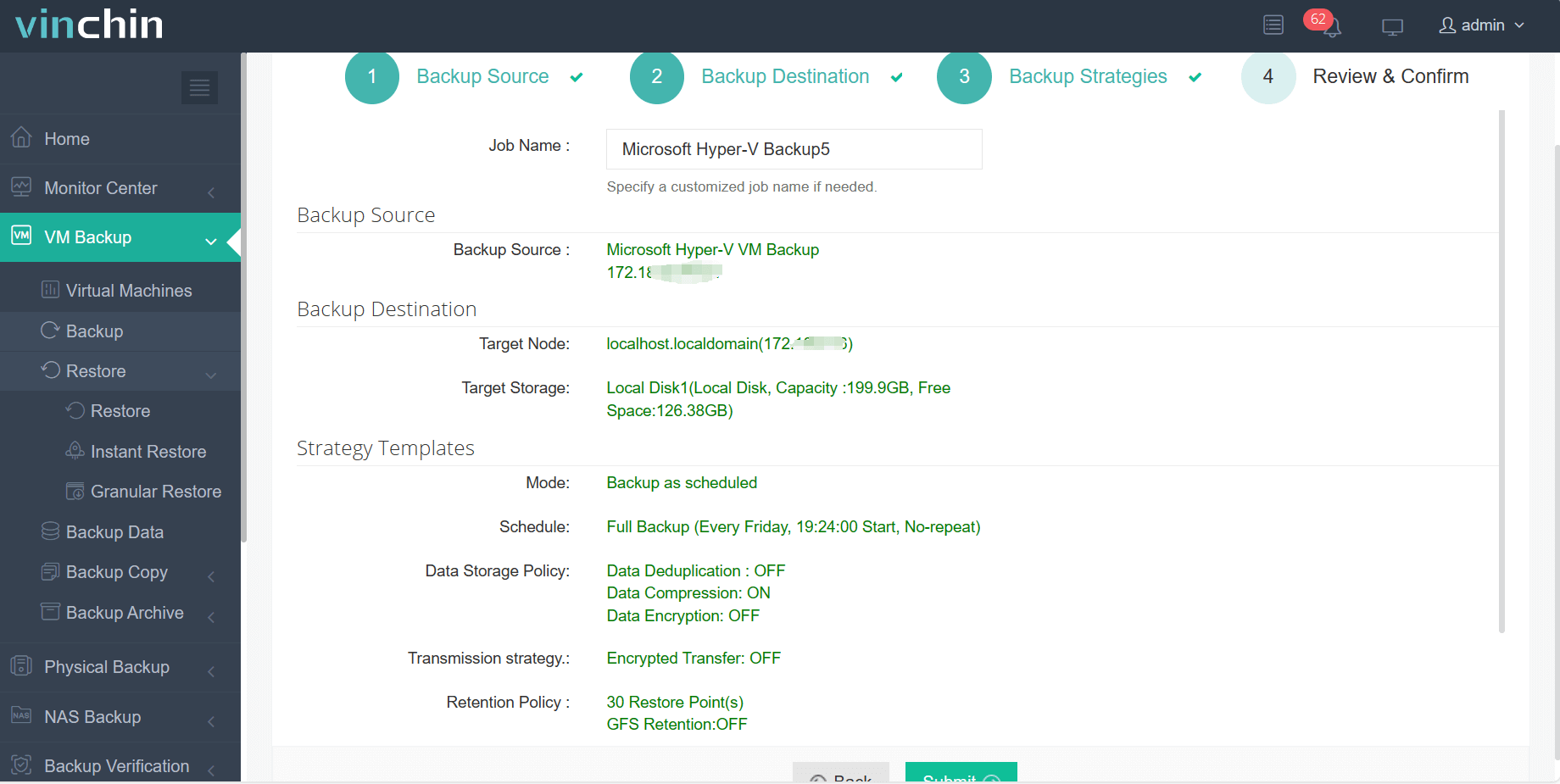
Vinchin not only protects your data but also simplifies your IT operations. With customers all over the globe and high product ratings, Vinchin is a trusted partner. Its interface is designed for clarity and speed. No complex commands or steep learning curves are required. Every step is clear and supported by detailed help center resources. Click the button below to download the installation package and deploy easily. Embrace strong Hyper-V security and ensure your data stays safe.
Hyper-V Security FAQs
1. What is Secure Boot in Hyper-V?
Secure Boot ensures that only trusted code runs during the VM boot process. It blocks unauthorized firmware and software from loading. You can use it following the steps below,
Open Hyper-V Manager > right-click the VM and select Settings > click Security in the left pane > ensure Enable Secure Boot is checked > choose the proper template: Microsoft Windows for Windows guests or Microsoft UEFI Certificate Authority (or Open Source Shielded VM) for Linux guests > click OK to save your settings
2. What are Shielded Virtual Machines?
Shielded VMs use encryption to protect VM data and configuration from unauthorized access. They are ideal for sensitive workloads.
3. How does Vinchin enhance Hyper-V security?
Vinchin can backup and migrate VMs quickly with features like speedkit, backup data retention, and granular restore. It simplifies protecting your virtual environment.
Conclusion
Hyper-V security is not an add-on; it is built into the system and must be managed well. The best practices include securing hosts, using Generation 2 VMs, enforcing network isolation, and applying strong authentication. Vinchin complements these practices by providing efficient backup and migration solutions. With robust protection measures, you can defend against data breaches and keep your operations running smoothly.
Share on: