-
Three commonly used service models in cloud computing
-
The advantages of cloud computing
-
What are the security risks in cloud computing?
-
How to manage cloud security risks?
-
Vinchin solution for virtual machine disaster recovery
-
Conclusion
Cloud computing is a computing model based on the Internet that enables convenient access to computing, storage, and software services without the need for local server deployment. It offers robust computing capabilities and solutions, revolutionizing the allocation of IT resources for businesses and driving numerous technological innovations.
Cloud computing features significant characteristics such as high scalability, virtualized deployment, large-scale clusters, pay-as-you-need, self-service provisioning, resource pooling, and service orientation. This new computing and service delivery model provides businesses and individuals with a more flexible, efficient, and cost-effective utilization of IT resources. It is precisely due to its many advantages that an increasing number of enterprises and organizations are opting for cloud disaster recovery to safeguard critical data. However, as cloud computing platforms become more widely adopted, the associated risks are also becoming increasingly apparent.
Three commonly used service models in cloud computing
1. Software as a Service (SaaS): SaaS platform providers deploy application software on their own servers. Customers can subscribe to the required application software services from the vendor based on their actual work needs. They pay the vendor fees based on the quantity and duration of the subscribed services. Through the internet, they can access the services provided by the SaaS platform provider.
2. Platform as a Service (PaaS): PaaS provides the development environment as a service. Developers use the vendor's code blocks to create their own applications. The platform is hosted in the cloud and accessed through a web browser.
3. Infrastructure as a Service (IaaS): IaaS offers basic computing resources, including virtualized servers, storage, and networking. Users can create their own virtual machines, storage, and network configurations through IaaS, with full control and administrative privileges. The IaaS provider is responsible for maintaining the hardware equipment and infrastructure, while the users are responsible for managing the operating system, applications, and data.
The advantages of cloud computing
1. Strong flexibility and scalability
2. Resource sharing and rational utilization of resources
3. Low cost and strong computing power
4. Versatile, fast and convenient
What are the security risks in cloud computing?
1. Virtualization Risks:
Unauthorized access and data loss
Known or unknown network attacks
System, configuration, vulnerability, and sensitive information leakage in mirrored templates
Lack of synchronization between residual information and policies during virtual machine migration
Malicious code
2. Cloud Storage Risks:
Incomplete deletion of user data backups and replicas
Inadequate clearance of user disk storage space after release
Risk of unauthorized mounting of volumes leading to unauthorized disclosure of user data.
3. Human-related Risks:
Untrustworthy internal users
Insufficient technical capabilities
Weak security awareness
4. Network Risks:
Risks of unauthorized network access
Risks of network threat traffic
Risks of unauthorized devices connecting to the internal virtual network of the platform
5. Management Risks:
Lack of clear roles and responsibilities
Inefficient workflow processes
Unclear work objectives
Inefficient integration of security technologies, security management, and security processes, resulting in low overall operational efficiency
Risks of non-compliant usage of operation and maintenance management accounts by related personnel
6. Host Risks:
Risks of firmware tampering
Risks of non-compliant operations
Insecure APIs
Risks of security policy not being synchronized with virtual machine migration
7. Operating System Risks:
Risks of improper security configuration and vulnerability handling in the operating system
8. Technical Risks:
Insufficient risk assessment
Account and service hijacking
Lack of audit logs, making it difficult to trace and track incidents
Low effectiveness in intelligence gathering and utilization, unable to detect advanced threats
Lack of monitoring, early warning, and automated response capabilities
9. Container Risks:
Risks of container escape attacks
Risks of security tampering or threat implantation in container images
Deficiencies in container security configuration
10. Password Service Risks:
Risks of key reuse leading to cracking and leakage
11. Distributed Components Risks:
Security risks associated with distributed components, processes, interfaces, and nodes
How to manage cloud security risks?
Strengthen identity and access management
Conduct assessment before selecting cloud service providers
Create dependency diagrams
Enhance network security
Vulnerability management and patch updates
Encrypt data transmission and storage
Establish backup and recovery plans
Perform regular testing (regression testing and penetration testing)
Implement continuous monitoring
Provide security awareness training to employees
Vinchin solution for virtual machine disaster recovery
To better protect your data, it is recommended to choose a professional data backup and recovery solution. As a professional data protection solution provider, Vinchin owns the leading disaster recovery technology to various virtualized platforms and provides reliable disaster recovery solutions to every client in many industries.
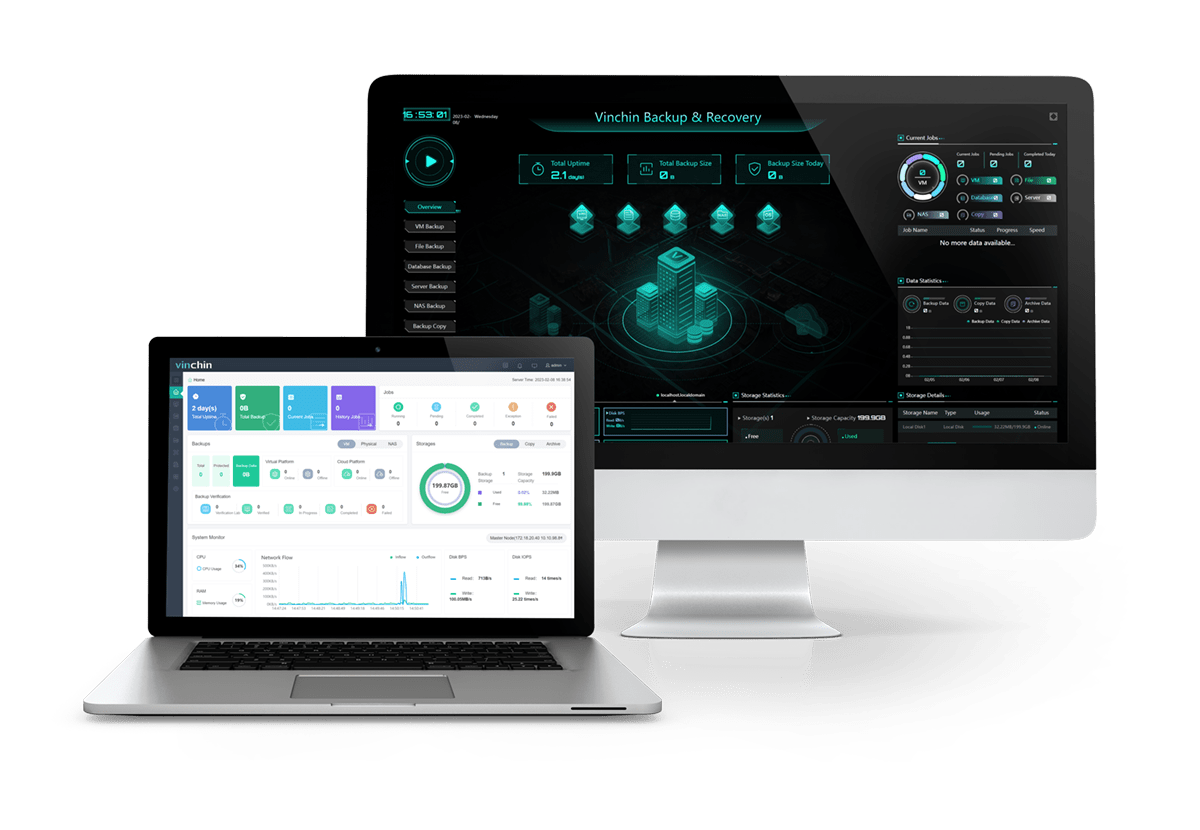
Vinchin Backup & Recovery is a professional solution which supports data backup of VM like VMware vSphere, Hyper-V, XenServer, XCP-ng, oVirt, RHV, OpenStack, etc. and other data like database, NAS, file server, etc.
Vinchin Backup & Recovery can not only meet the data backup requirements of traditional information business environments (offsite backup), but also seamlessly support data protection by achiving the backup data to the public cloud.
You can archive the local backup file to cloud object storage for long term retention and DR with Vinchin Backup Archive. In case the primary backup got destroyed together with production data, you can transfer back the VM data from archived backup file in the cloud and restore to onsite production system. Vinchin Backup & Recovery supports the mainstream cloud platforms like AWS S3, Microsoft Azure, Wasabi, and MinIO as cloud archive destination.
Vinchin Backup & Recovery has been selected by thousands of companies and you can also start to use this powerful system with a 60-day full-featured trial! Also, contact us and leave your needs, and then you will receive a solution according to your IT environment.
Conclusion
The many benefits of working in the cloud can easily make us overlook its few manageable risks. Cost savings, scalability, and coupled with the seamless ease with which people can work remotely, make cloud computing the right choice for many of today’s leading companies. Choosing the right technology and management for your business will reduce the security risk in cloud computing.
To efficiently protect your data, you can choose Vinchin Backup & Recovery to easily backup and recover your critical data. Don’t miss the free trial.
Share on: