-
Common types of cyber attacks
-
The difference between network recovery and disaster recovery
-
How to recover from a cyber attack?
-
Simplify your cybersecurity with Vinchin Backup & Recovery
-
Recovery after cyber attack FAQs
-
Conclusion
In today's digitalized world, businesses are facing an increasing threat of cyber attacks. These attacks not only affect the security of a company's data, but can also lead to loss of productivity, financial loss, and severe damage to a company's reputation. Therefore, understanding the types of cyberattacks, their impact, and how to recover from a cyber attack has become a crucial part of an organization's cybersecurity strategy.
Common types of cyber attacks
Cyberattacks come in a variety of forms, each of which can have far-reaching effects on an organization. Below are a few of the most common and destructive types of cyberattacks:
Malware: Malware is a type of software that is used to damage or invade a computer system, stealing data, damaging the system, or performing other malicious operations without the user's knowledge.
Ransomware: Ransomware works by encrypting an organization's critical data and demanding a ransom to unlock it. This type of attack is usually carried out in a very stealthy manner, and once infected, an organization will face the dilemma of paying the ransom or losing the data forever.
Phishing: Phishing is an email, text message, or phone call that masquerades as a legitimate organization, enticing the user to provide sensitive information or download a malicious attachment. This type of attack often uses social engineering tactics to make the target vulnerable.
Distributed Denial of Service (DDoS) Attacks: These attacks send a large number of invalid requests to the target server, causing the server to become overloaded and crash, making it impossible for the organization's online services to operate normally.
The difference between network recovery and disaster recovery
Although the terms“cyber recovery”and“disaster recovery”are used interchangeably in some cases, they have different emphases:
Disaster Recovery
Disaster recovery focuses on ensuring that business operations can be quickly resumed in the event of a major incident, such as a natural disaster, system crash, or cyber attack. Disaster recovery plans focus on system recovery, data protection, and minimizing downtime.
Network Recovery
Network recovery focuses more on restoring a network environment that has been attacked or compromised, ensuring that all network components and systems can be restored to normal operation, preventing data leakage and ensuring information security.
How to recover from a cyber attack?
When a business experiences a cyber attack, a quick and effective recovery process is essential. Below are the key steps:
⚡Rapid Response:
Immediately activate an incident response plan upon detecting an attack. Identify the nature and scope of the breach, affected systems, and implement containment measures to prevent further spread.
⚡Contain the Attack:
Isolate affected systems or networks, disconnect them from external access, and prevent further data leaks.
⚡Restore Backup Data:
If a backup system is in place, swiftly restore data from a secure and uncompromised backup source to ensure operational continuity.
⚡Restore Critical Operations:
Ensure business operations continue running using backup solutions even if some systems remain affected.
⚡Investigate the Source of the Attack:
Conduct a detailed analysis to determine the root cause, identify vulnerabilities, and implement patches to prevent future occurrences.
⚡Improve Security Measures:
Strengthen network security by updating protocols, enhancing employee security awareness, upgrading firewalls, and implementing advanced data encryption.
Simplify your cybersecurity with Vinchin Backup & Recovery
In today's digital landscape, protecting your business from cyber threats is crucial, and a solid backup and recovery strategy is the first line of defense. Vinchin Backup & Recovery delivers an advanced, reliable solution with powerful features like agentless backup, instant recovery, and built-in ransomware protection. This ensures that your critical data stays safe while minimizing downtime and keeping your operations running smoothly, even in the face of cyber incidents.
Tailored for virtual environments, Vinchin supports platforms such as Proxmox, VMware, Hyper-V, XenServer, XCP-ng, oVirt, RHV, and more. It offers flexible VM backup, quick recovery, and seamless V2V migration, allowing businesses to protect, manage, and recover virtualized data effortlessly.
Simple Steps to Backup Your VMs
Vinchin makes the process easy with just a few simple steps:
✅ 1. Select VMs on the Host
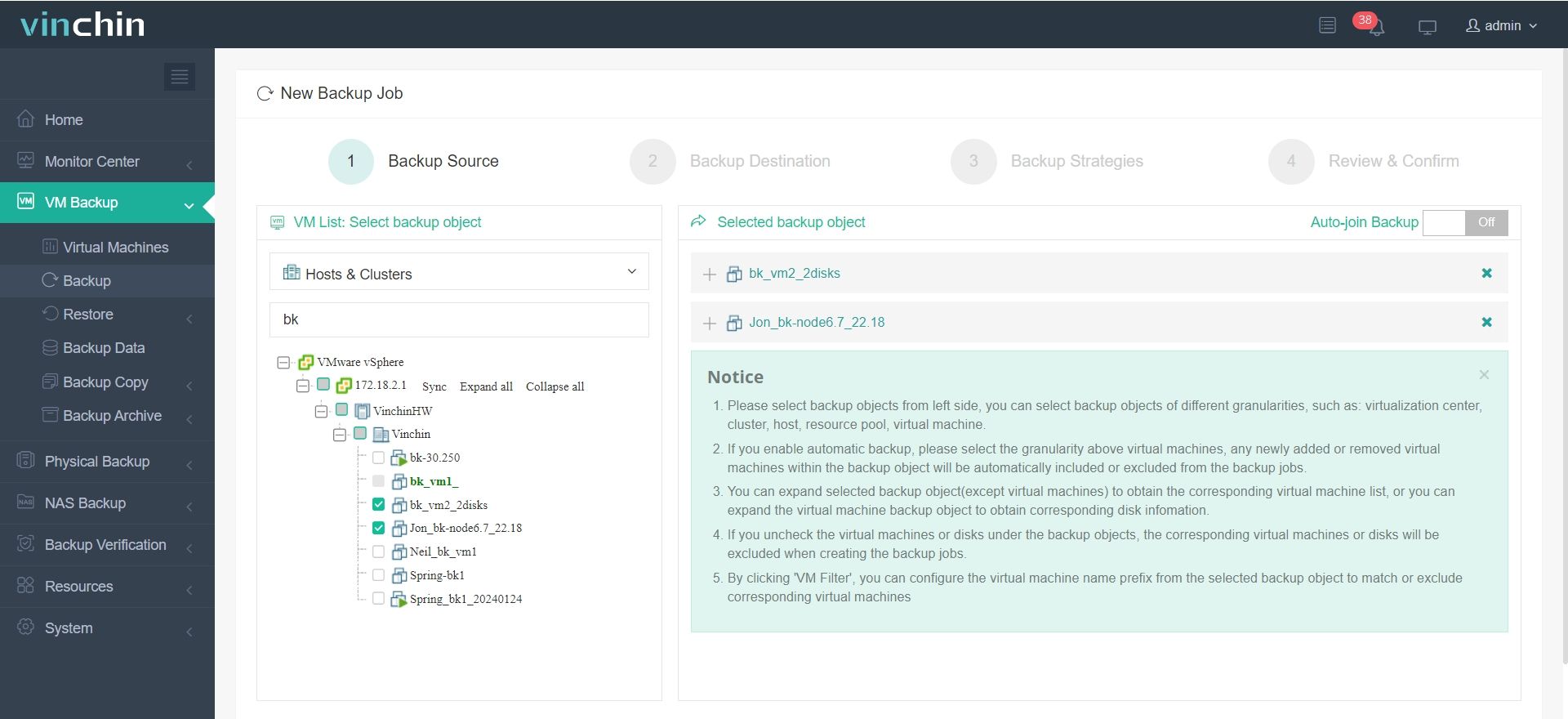 ✅ 2. Choose Your Backup Destination
✅ 2. Choose Your Backup Destination
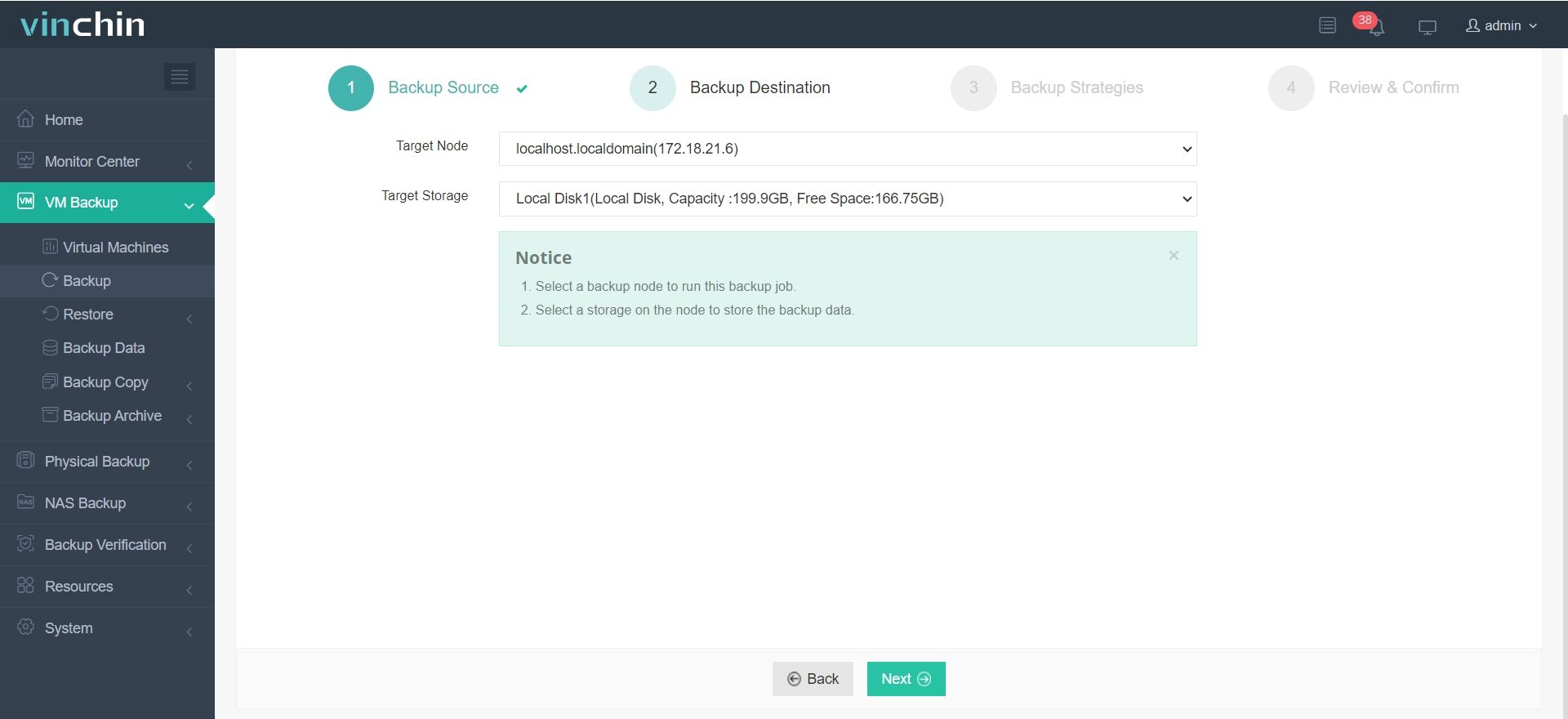 ✅ 3. Pick Your Backup Strategy
✅ 3. Pick Your Backup Strategy
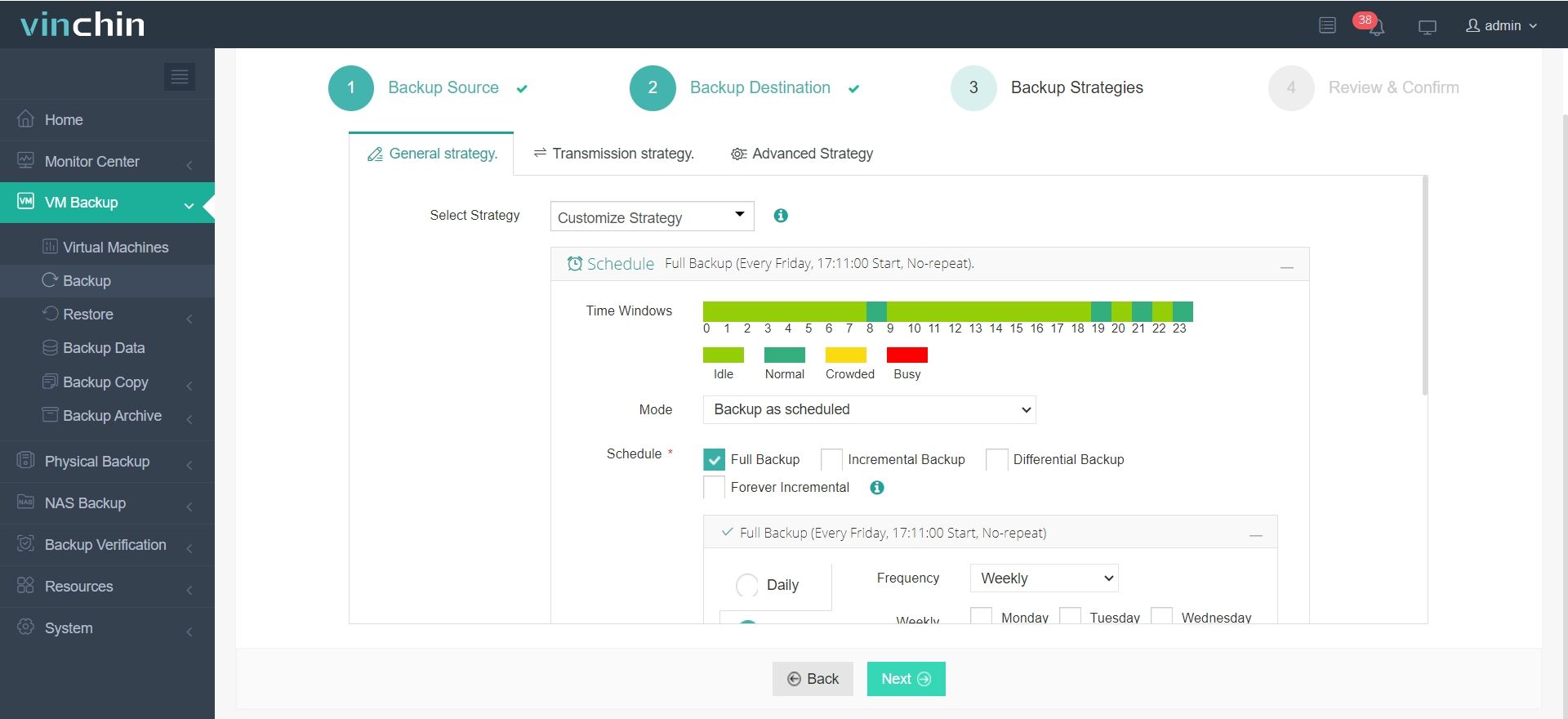 ✅ 4. Submit the Job and Let Vinchin Work
✅ 4. Submit the Job and Let Vinchin Work
To make the decision even easier, Vinchin offers a 60-day free trial, giving users the opportunity to experience its robust backup and recovery features in a live environment. Don't miss the chance to protect your business with Vinchin! Feel free to contact us!!!!
Recovery after cyber attack FAQs
Q1: What is the importance of data protection and what are the measures?
A1: Strengthen data encryption technology to ensure that even if data is stolen, it is difficult to decipher.
Implement strict access control policies to limit access to sensitive information.
Q2: What is the role of a Business Continuity Plan (BCP)?
A2: Develop a detailed business continuity plan to ensure that critical business functions can continue to operate or recover quickly in the event of an attack.
Test and update the BCP to ensure that it is effective and viable in the event of an actual emergency.
Conclusion
In conclusion, protecting businesses from cyber threats requires a robust backup and recovery strategy. Vinchin Backup & Recovery offers a reliable solution to ensure data protection, minimize downtime, and facilitate seamless recovery, strengthening organizations’ cybersecurity and operational resilience.
Share on: